NETWORK SECURITY MONITORING
The solution to identify and prevent Cyber attacks and intrusions to the most robust network in the market. This solution is based on the analysis of customer traffic, consists of two types of scopes:
Advanced threat protection (ATP) refers to a category of security solutions that defend against sophisticated malware or hacking-based attacks targeting sensitive data.
Advanced threat protection solutions can be available as software or as managed services.
ATP solutions can differ in approaches and components, but most include some combination of endpoint agents, network devices, email gateways, malware protection systems, and a centralized management console to correlate alerts and manage defenses.
There are three primary goals of advanced threat protection: early detection (detecting potential threats before they have the opportunity to access critical data or breach systems), adequate protection (the ability to defend against detected threats swiftly), and response (the ability to mitigate threats and respond to security incidents).
To achieve these goals, advanced threat protection services and solutions must offer several components and functions for comprehensive ATP:
Real-time visibility – Without continuous monitoring and real-time visibility, threats are often detected too late. When damage is already done, response can be tremendously costly in termsof both resource utilization and reputation damage.
Context – For true security effectiveness, threat alerts must contain context to allow security teams to effectively prioritize threats and organize response.
Data awareness – It’s impossible to determine threats truly capable of causing harm without first having a deep understanding of enterprise data, its sensitivity, value, and other factors that contribute to the formulation of an appropriate response. When a threat is detected, further analysis may be required.
Security services offering ATP typically handle threat analysis, enabling enterprises to conduct business as usual while continuous monitoring, threat analysis, and response occurs behind the scenes. Threats are typically prioritized by potential damage and the classification or sensitivity of the data at risk. Advanced threat protection should address three key areas:
- Halting attacks in progress or mitigating threats before they breach systems.
- Disrupting activity in progress or countering actions that have already occurred as a result of a breach.
- Interrupting the lifecycle of the attack to ensure that the threat is unable to progress or proceed.
The IDS is an intrusion detection system, used to identify unallowed access to the network. The SGA Works as a sensor that allows us to inspect in depth the data in transit in the network of the client, thanks to this we can identify attacks, malicious traffic, etc. This type of solution must work together with a Firewall because the IDS does not have the functionality to block an attack, only to identify it.
The validation of traffic occurs by two different methods that allow us to have a very wide panorama of validation, these methods are:
Heuristics: Determines normal network activity, such as the order of bandwidth used, protocols, ports, and devices that are generally interconnected, and generates alert about variations.
Advanced signatures: Scans all packets on the network, and compares them against known, preconfigured attack patterns. These patterns are called signatures. Due to this technique, there is a period of time between the discovery of the attack and its pattern, due to the hardware configuration of the sensor this validation occurs almost in real time.
The implementation of this solution does not imply modification of the client's existing infrastructure configuration.
Our IDS and IPS solutions, based on proprietary and open source solutions, allow for a combination of heterogeneous, synchronized and centrally managed and combined systems as well as integration with traffic reconstruction systems, firewalls, honeypots, etc. In addition, of course, we count on the support of the facilities we have built and the sites and infrastructure that they protect today, being one of the most robust solutions in the market.
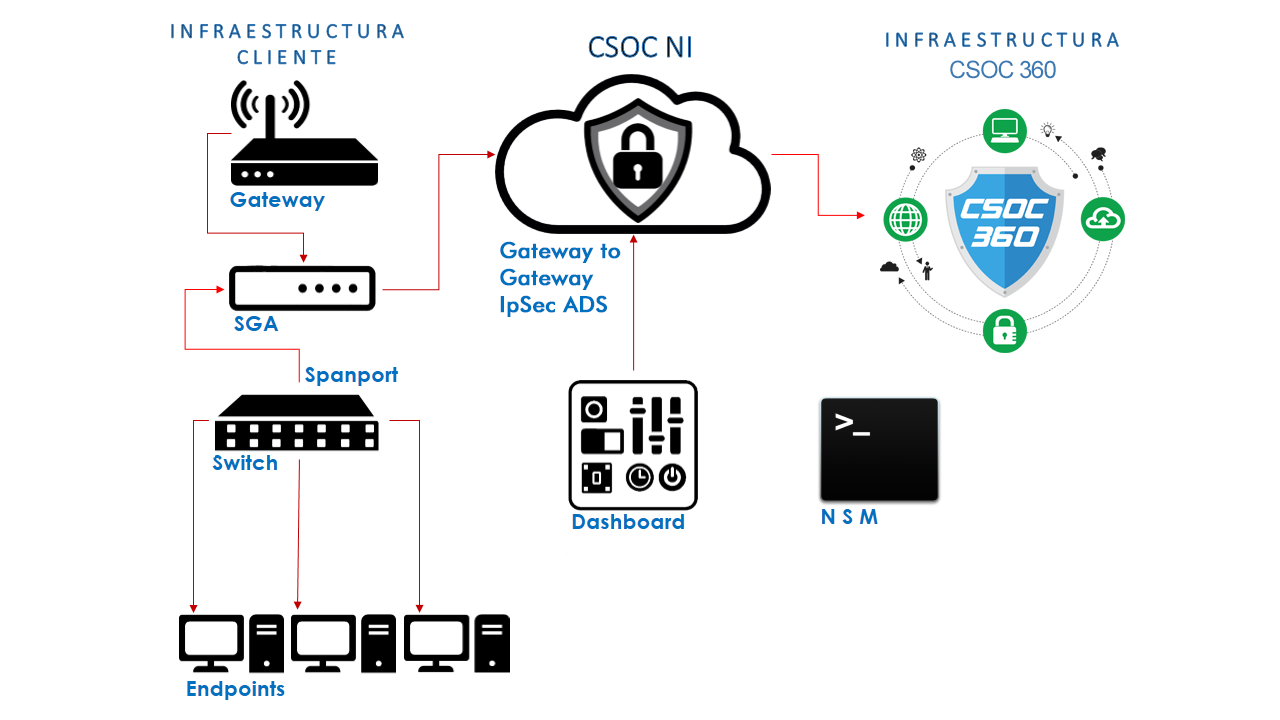
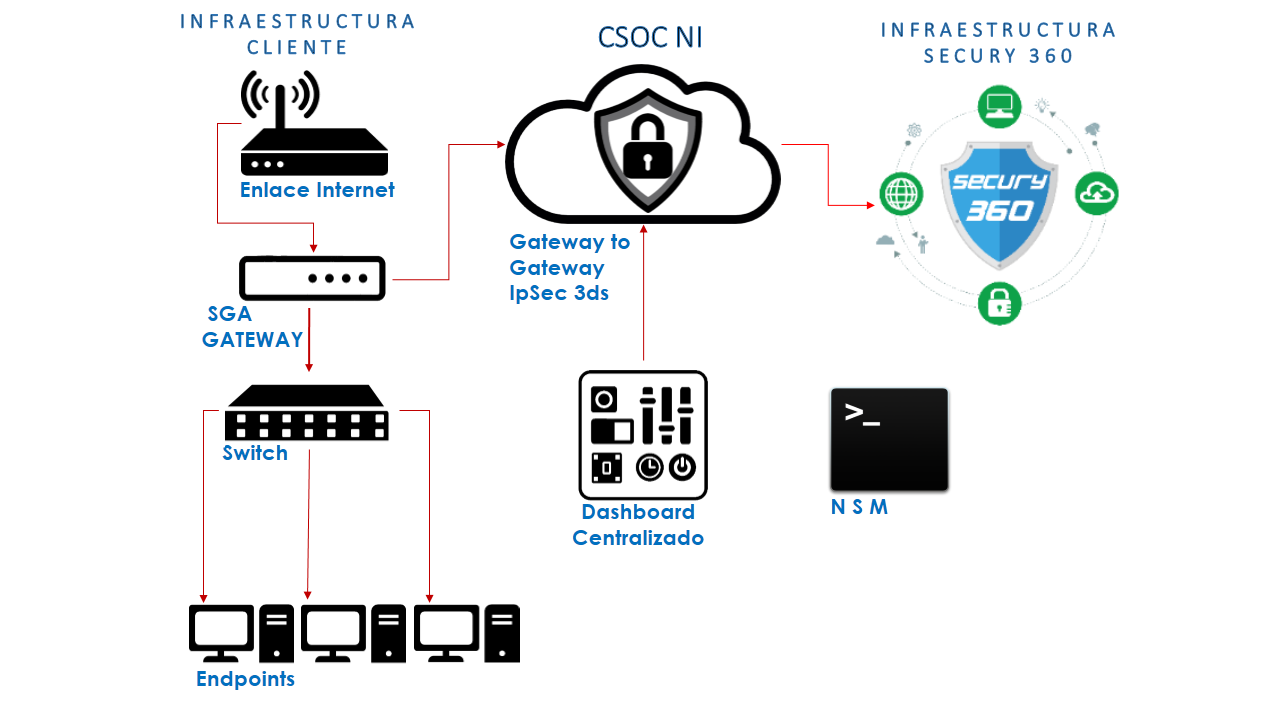
With the growing dependence on technology, with more and more information circulating on the network, information of great relevance for organizations such as electronic invoices. It is becoming more and more necessary and essential to have mechanisms that protect this type of information.
Security Gateway Appliance (SGA), fulfills this purpose. It has features that allow you to protect your networks in a comprehensive way. Provides protection to your communications and your equipment from a single device. In addition, we have different models to protect from small networks to very complex corporate networks.
Being ours SGA the main gateway of the client's network communications, blocks attacks and access by illegitimate users. Unlike the IDS that monitors them. This service is categorized by the way malicious traffic is detected:
Based on signatures: Compares traffic with known attack signatures, you must have the signature list updated.
Based on policies: Strict security policies are defined, if traffic is allowed the IPS allows the traffic, if it is not blocked it.
Based on anomalies+: This method is the one that most false positives generate because it is very difficult that it is normal or standard. In this mode we find two options:
Statistical detection of abnormalities: It analyzes all the traffic during a certain time, after this time creates a line of what is "normal or standard". After this period ends if the behavior varies greatly compared to the rule created, it is taken as a possibility of attack.
Non-Statistical Detection of Abnormalities: In this option the Administrator defines the line of what is "normal or standard" that will be the basis for traffic comparison.
In summary, the IPS adds the possibility of blocking attacks and also proactively protects the network, while the IDS does not allow to block and reactively protects the network.
Our IDS and IPS solutions, based on proprietary and open source solutions, allow for a combination of heterogeneous, synchronized and centrally managed and combined systems as well as integration with traffic reconstruction systems, firewalls, honeypots, etc. In addition, of course, we count on the support of the facilities we have built and the sites and infrastructure that they protect today, being one of the most robust solutions in the market.
What is SIEM?
Security Information and Event Management (SIEM) is a set of tools and services offering a holistic view of an organization’s information security.
SIEM tools provide:
- Real-time visibility across an organization’s information security systems.
- Event log management that consolidates data from numerous sources.
- A correlation of events gathered from different logs or security sources, using if-then rules that add intelligence to raw data.
- Automatic security event notifications. Most SIEM systems provide dashboards for security issues and other methods of direct notification.
SIEM works by combining two technologies:
A) Security information management (SIM), which collects data from log files for analysis and reports on security threats and events, and
B) Security event management (SEM), which conducts real-time system monitoring, notifies network admins about important issues and establishes correlations between security events.
The security information and event management process can be broken down as follows:
Data collection: All sources of network security information, e.g., servers, operating systems, firewalls, antivirus software and intrusion prevention systems are configured to feed event data into a SIEM tool.Most modern SIEM tools use agents to collect event logs from enterprise systems, which are then processed, filtered and sent them to the SIEM. Some SIEMs allow agentless data collection. For example, Splunk offers agentless data collection in Windows using WMI.
Policies: A profile is created by the SIEM administrator, which defines the behavior of enterprise systems, both under normal conditions and during pre-defined security incidents. SIEMs provide default rules, alerts, reports, and dashboards that can be tuned and customized to fit specific security needs.
Data consolidation and correlation: SIEM solutions consolidate, parse and analyze log files. Events are then categorized based on the raw data and apply correlation rules that combine individual data events into meaningful security issues.
Notifications: If an event or set of events triggers a SIEM rule, the system notifies security personnel.
Network security monitoring is the collection, analysis and escalation of the prompts and warnings to detect and respond to intrusions that are present.
Postech IT Solution Provider NSM Threat Protection System is one solution comprehensive tool that helps organizations locate, understand, and neutralize advanced threats.
Provides an intuitive graphical interface capable of detecting, assigning IDs, investigating and remedy attacks.
NSM continuously monitors and relates traffic on our organization's WAN or LAN networks, email, files, development code and internal or external plant devices.
Attacks that are invisible to traditional defense mechanisms (Cyber-Attack Kill Chain) regardless of the type, stage, vector or attack tool used.
The frame of reference used by NSM dramatically reduces detection time, which helps to minimize damage to the organization.
NSM bases its operation on the complete analysis of network captures, covering accesses to the internet, email output and DNS servers, etc., as well as points critics of the internal network. Traffic is passively and non-intrusively inspected. There are no changes or modifications to the architecture or network configuration.
Through a wide coverage of systems, internal and external network points, you can count with real-time threat detection as well as raw data capture and logging and Metadata that can be additionally used in a forensic investigation and analysis.



