URL FILTERING
The solution to identify and prevent Cyber attacks and intrusions to the most robust network in the market. This solution is based on the analysis of customer traffic, consists of two types of scopes:
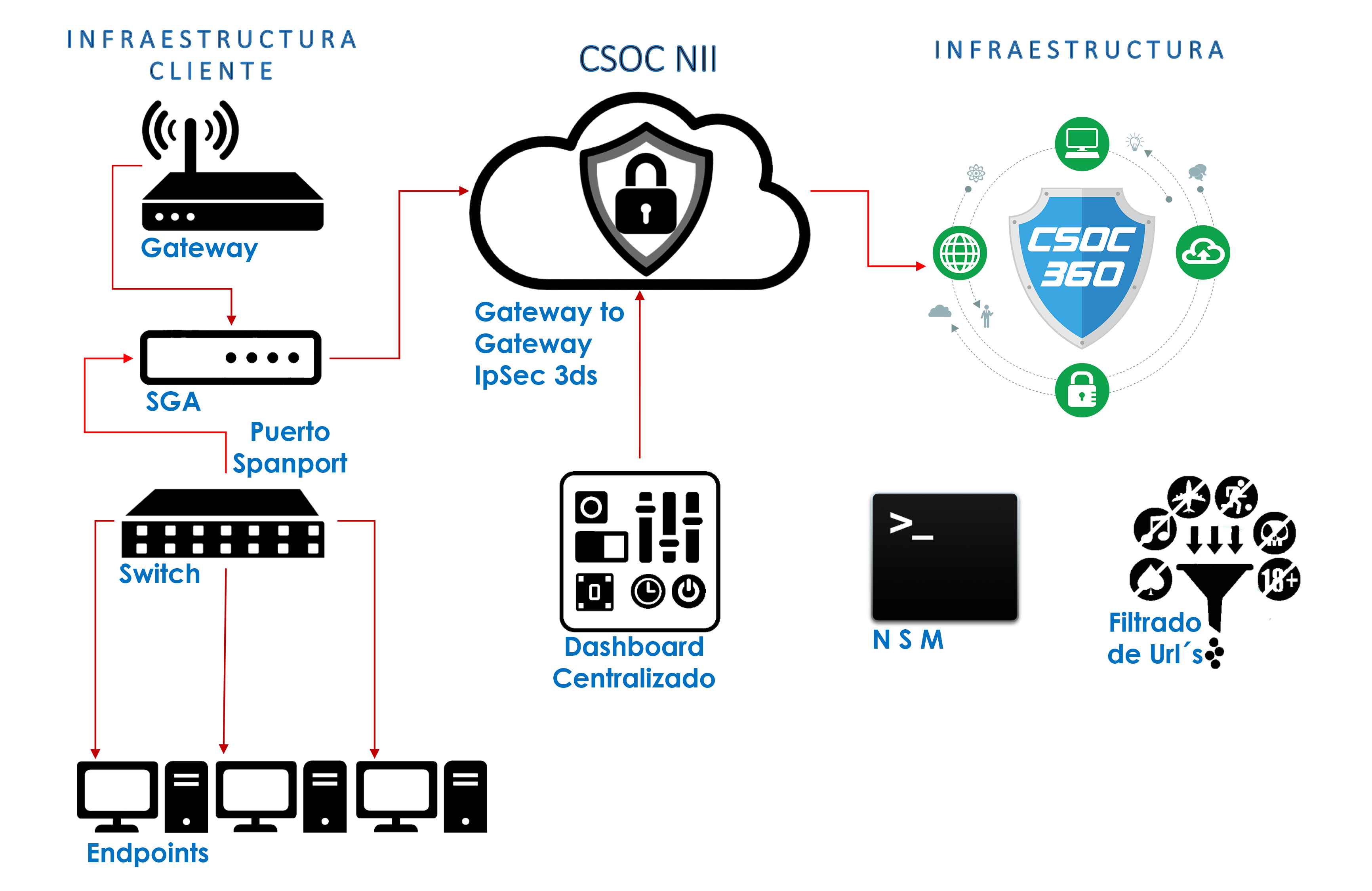
The IDS is an intrusion detection system, used to identify unallowed access to the network. The SGA Works as a sensor that allows us to inspect in depth the data in transit in the network of the client, thanks to this we can identify attacks, malicious traffic, etc. This type of solution must work together with a Firewall because the IDS does not have the functionality to block an attack, only to identify it.
The validation of traffic occurs by two different methods that allow us to have a very wide panorama of validation, these methods are:
Heuristics: Determines normal network activity, such as the order of bandwidth used, protocols, ports, and devices that are generally interconnected, and generates alert about variations.
Advanced signatures: Scans all packets on the network, and compares them against known, preconfigured attack patterns. These patterns are called signatures. Due to this technique, there is a period of time between the discovery of the attack and its pattern, due to the hardware configuration of the sensor this validation occurs almost in real time.
The implementation of this solution does not imply modification of the client's existing infrastructure configuration.
Our IDS and IPS solutions, based on proprietary and open source solutions, allow for a combination of heterogeneous, synchronized and centrally managed and combined systems as well as integration with traffic reconstruction systems, firewalls, honeypots, etc. In addition, of course, we count on the support of the facilities we have built and the sites and infrastructure that they protect today, being one of the most robust solutions in the market.
Being ours SGA the main gateway of the client's network communications, blocks attacks and access by illegitimate users. Unlike the IDS that monitors them. This service is categorized by the way malicious traffic is detected:
Based on signatures: Compares traffic with known attack signatures, you must have the signature list updated.
Based on policies: Strict security policies are defined, if traffic is allowed the IPS allows the traffic, if it is not blocked it.
Based on anomalies: This method is the one that most false positives generate because it is very difficult that it is normal or standard. In this mode we find two options:
Statistical detection of abnormalities: It analyzes all the traffic during a certain time, after this time creates a line of what is "normal or standard". After this period ends if the behavior varies greatly compared to the rule created, it is taken as a possibility of attack.
Non-Statistical Detection of Abnormalities: In this option the Administrator defines the line of what is "normal or standard" that will be the basis for traffic comparison.
In summary, the IPS adds the possibility of blocking attacks and also proactively protects the network, while the IDS does not allow to block and reactively protects the network.
Our IDS and IPS solutions, based on proprietary and open source solutions, allow for a combination of heterogeneous, synchronized and centrally managed and combined systems as well as integration with traffic reconstruction systems, firewalls, honeypots, etc. In addition, of course, we count on the support of the facilities we have built and the sites and infrastructure that they protect today, being one of the most robust solutions in the market.
Network security monitoring is the collection, analysis and escalation of the prompts and warnings to detect and respond to intrusions that are present.
Postech IT Solution Provider NSM Threat Protection System is one solution comprehensive tool that helps organizations locate, understand, and neutralize advanced threats.
Provides an intuitive graphical interface capable of detecting, assigning IDs, investigating and remedy attacks.
NSM continuously monitors and relates traffic on our organization's WAN or LAN networks, email, files, development code and internal or external plant devices.
Attacks that are invisible to traditional defense mechanisms (Cyber-Attack Kill Chain) regardless of the type, stage, vector or attack tool used.
The frame of reference used by NSM dramatically reduces detection time, which helps to minimize damage to the organization.
NSM bases its operation on the complete analysis of network captures, covering accesses to the internet, email output and DNS servers, etc., as well as points critics of the internal network. Traffic is passively and non-intrusively inspected. There are no changes or modifications to the architecture or network configuration.
Through a wide coverage of systems, internal and external network points, you can count with real-time threat detection as well as raw data capture and logging and Metadata that can be additionally used in a forensic investigation and analysis.
The content filter is used to collect information from computer equipment and mobile devices that access internet sites from the networks of our infrastructure and in this way to be able to census and register their activities, this information is available at all times for Customers and is included within the weekly delivery reports.