NSM
NSM (Network Cyber-Security Monitoring) Network security monitoring is the collection, analysis and scaling of indications and warnings to detect and respond to intrusions that are present. The POSTECH NSM threat protection system is a comprehensive solution that helps organizations locate, understand, and neutralize advanced threats. It provides a novel, pre-integrated platform that can detect, prioritize, investigate and remedy attacks.
NSM continuously monitors web traffic, email, files, code, internal traffic and devices on the network. Attacks that are invisible to traditional defense mechanisms (Cyber-attack Kill Chain), regardless of the type, stage, vector or attack tool used. The frame of reference used by NSM dramatically reduces detection time, which helps to minimize damage to the organization.
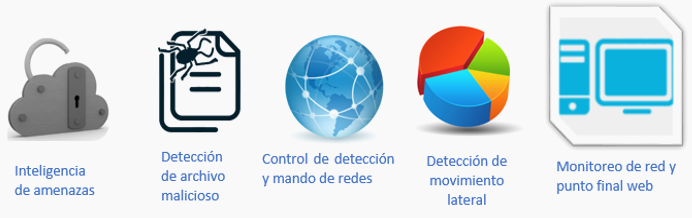
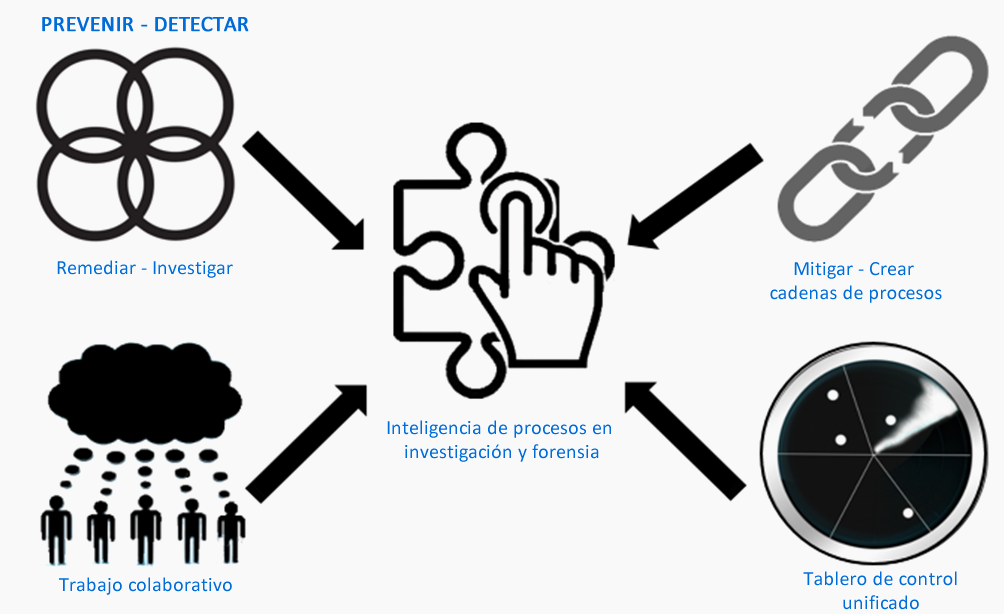
NSM integrates monitoring, detection, merger, investigation, forensic analysis for malware detection and remediation on a single, threat-focused SOC platform, the solution generates actionable intelligence that provides tools to eliminate malware, recover and harden the environment, and Protect the organization against future attacks.
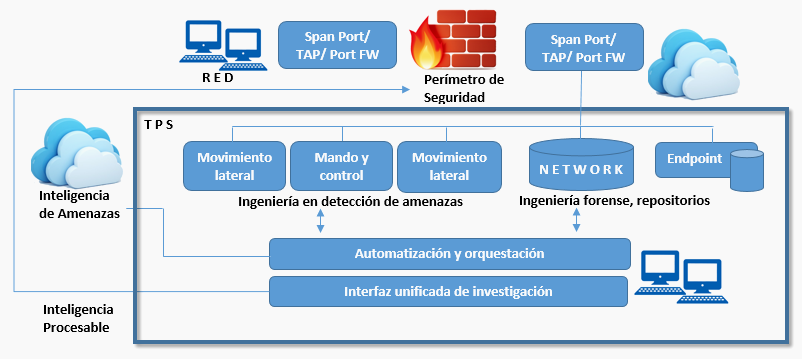
NSM bases its analysis on the complete analysis of catches of the network, covering: Internet access, e-mail and DNS servers, etc., as well as the critical points of the internal network. Traffic is passively and non-intrusively inspected. No changes or modifications to the architecture or network configuration are required.
Through extensive coverage of systems, internal and external network points, real-time threat detection can be achieved, as well as the capture and recording of raw data and metadata that can then be used in forensic research and analysis.
Performance and high-speed pre-processing includes decoding, sorting and filtering protocols. The traffic is then forwarded to the dedicated detection modules. For example, HTTP and HTNSM traffic is sent to the Command and Control detection module, and the received SMTP mail is sent to the malware detection module.
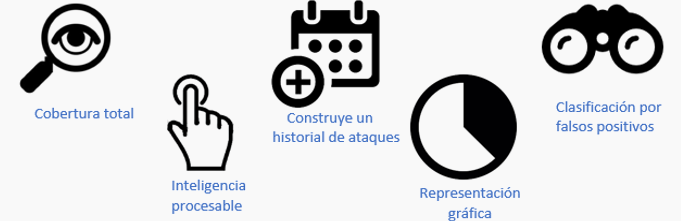
What benefits does NSM have?
- Distribution charts in signatures, addresses, source IP and destination IP.
- Events by protocol and assignment.
- List of sensors
- Detailed time lines that include full package capture.
- Hierarchical events by severity (high, medium and low).
- Counting of events by time and sensor.
- Severity of events over time.
- Counting of events by time by sensor.
- Semantic Searches.
- Smart notifications - configurable alerts that will respond to specific paging, email, call or text messaging scenarios by a network administrator.
- It can contain several sensors and centralize the information of the same, as well as to graph them.

